Get Started: IoT SSH Web Free Trial - Remote Access!
Ever dreamt of controlling your smart devices from anywhere in the world, without burning a hole in your pocket? Imagine a world where accessing your IoT devices is not only secure and reliable but also completely free, leveraging the power of SSH through web interfaces.
The convergence of IoT (Internet of Things), SSH (Secure Shell), and web technologies is rapidly transforming how we interact with our connected devices. This synergy offers a powerful and cost-effective solution for remote access, management, and monitoring of IoT devices. The ability to access and control these devices through a web browser, using the secure SSH protocol, opens up a world of possibilities for developers, tech enthusiasts, and everyday users alike. This approach eliminates the need for complex and expensive software solutions, putting the power of remote IoT management directly at your fingertips. This article delves into the intricacies of this technological convergence, exploring the benefits, security considerations, and practical applications of IoT SSH web solutions.
| Category | Information |
|---|---|
| Topic | IoT SSH Web Solutions |
| Description | Exploration of remote access and management of IoT devices using SSH through web interfaces. |
| Key Technologies | IoT, SSH (Secure Shell), Web technologies, Android |
| Benefits | Secure remote access, cost-effectiveness, simplified management, remote monitoring |
| Security | Importance of OS and SSH software updates, vulnerability patching |
| Applications | Remote monitoring, file management, secure authentication |
| Related Technologies | Reverse proxy tunnels, VNC, RDP, VPN |
| Additional Features | Alerting, metric monitoring, access control, key management |
One of the most significant advantages of utilizing SSH for web-based IoT access is the enhanced security it provides. SSH employs robust encryption algorithms to protect data transmitted between the user and the IoT device, mitigating the risk of eavesdropping and unauthorized access. This is particularly crucial when dealing with sensitive data or devices that control critical infrastructure. Furthermore, SSH supports various authentication methods, including password-based authentication and key-based authentication, allowing for a more secure and flexible access control system. By implementing strong authentication measures and regularly updating SSH software, users can significantly reduce the risk of security breaches and ensure the integrity of their IoT deployments.
- Stream Terrifier 3 For Free Your Ultimate Guide To Unleashing The Horror
- How Old Are P Diddys Twins A Deep Dive Into Their Lives And Legacy
The integration of web interfaces with SSH access further simplifies the management and monitoring of IoT devices. Web-based interfaces provide a user-friendly and intuitive way to interact with devices, eliminating the need for specialized software or command-line expertise. This makes it easier for users of all skill levels to access and control their IoT devices from anywhere with an internet connection. Moreover, web interfaces can be customized to provide real-time monitoring of device status, performance metrics, and alerts, enabling proactive maintenance and troubleshooting. This combination of security and ease of use makes IoT SSH web solutions an attractive option for a wide range of applications.
Consider the scenario of remotely monitoring a Raspberry Pi, a popular single-board computer often used in IoT projects. By leveraging SSH through a web interface, users can access the Raspberry Pi's command line, view system logs, and monitor resource utilization from any web browser. This allows for convenient troubleshooting and maintenance without the need to physically access the device. Similarly, users can remotely upload and download files to and from their Raspberry Pi using an SSH client such as FileZilla or PuTTY, further enhancing the device's manageability. This level of remote access and control is invaluable for IoT deployments in remote locations or in situations where physical access is limited.
The combination of IoT, SSH, web interfaces, and even Android platforms creates a powerful ecosystem for tech enthusiasts, developers, and everyday users. Imagine controlling your home automation system from your Android phone via a secure SSH connection through a web interface, all while enjoying the flexibility and cost-effectiveness of free software solutions. This convergence empowers users to build and manage their own smart environments with greater control and security. It also fosters innovation by providing developers with a versatile platform for creating new and exciting IoT applications.
- Mkv Cinemas Your Ultimate Streaming Experience Redefined
- Mp4moviez Com Your Ultimate Guide To Streaming Movies Online
To ensure the security of your IoT SSH web deployments, it is essential to follow best practices for system administration and security. Regularly updating your IoT device's operating system and SSH software is crucial for patching known security vulnerabilities. This includes installing security updates and patches for the OS and SSH software as soon as they become available. Furthermore, it is important to use strong passwords or SSH keys for authentication and to restrict access to authorized users only. Implementing a firewall and intrusion detection system can also help to protect your IoT devices from malicious attacks. By taking these precautions, you can minimize the risk of security breaches and ensure the long-term integrity of your IoT deployments.
Understanding the concept of a reverse proxy tunnel is also crucial for securely accessing SSH clients behind a NAT router or firewall. A reverse proxy tunnel creates an SSH connection from the SSH client to a public SSH server, allowing users to access the client from anywhere on the internet. This eliminates the need to expose the SSH client directly to the internet, which can significantly improve security. The reverse proxy acts as an intermediary, forwarding traffic between the user and the SSH client while hiding the client's internal IP address and network configuration. This technique is particularly useful for accessing IoT devices that are located behind firewalls or in private networks.
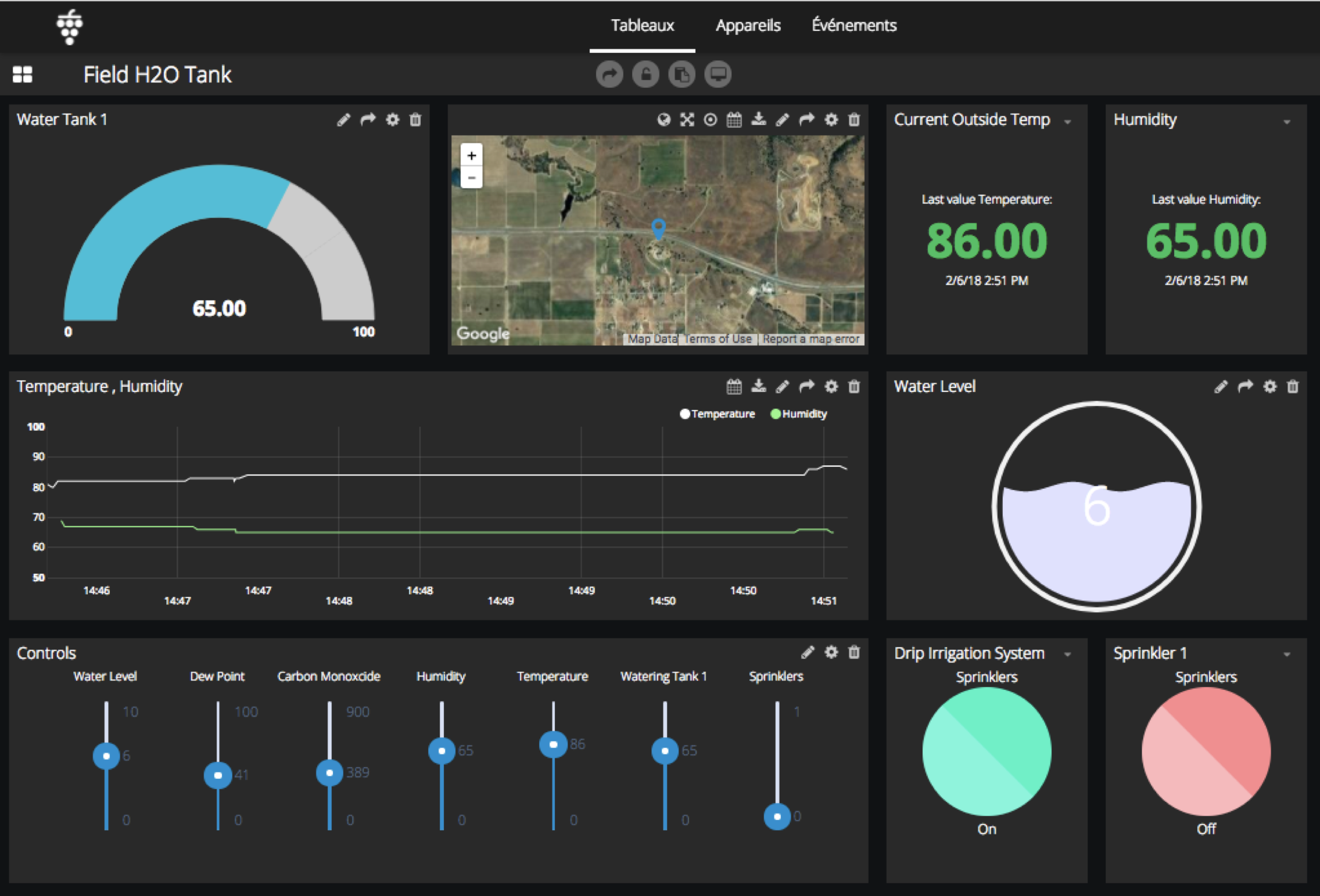
IoT remote monitoring plays a crucial role in ensuring the reliable operation of connected devices. Remote monitoring involves the surveillance of smart technology as they operate in tandem with each other. Typically, an administrator uses a software program or application to view the status of each IoT device from a centralized digital control center. This allows for real-time monitoring of device performance, identification of anomalies, and proactive troubleshooting. By leveraging SSH through web interfaces, users can gain instant, secure access to their IoT devices and monitor their performance from anywhere in the world. This combination of remote monitoring and secure access empowers users to manage their IoT deployments more effectively and efficiently.
Several commercial solutions offer features like 30-day free trials with credits for risk-free experimentation, 24/7 managed support, SSH/web SSH access, and IoT backends. These solutions often utilize cloud VPS (Virtual Private Servers) to build the backend infrastructure, providing a scalable and reliable platform for managing IoT devices. While these commercial solutions offer convenience and comprehensive features, it is also possible to build your own IoT SSH web solution using open-source tools and cloud services. This approach requires more technical expertise but can offer greater flexibility and cost savings.
The architecture of an IoT SSH web server primarily comprises three key components: the SSH client, the SSH server, and the network infrastructure which binds them together. The SSH client runs on the IoT device and initiates a secure connection to the SSH server. The SSH server acts as an intermediary, authenticating users and forwarding traffic to the IoT device. The network infrastructure provides the communication channels between the client, server, and user. Understanding the roles and responsibilities of these components is essential for designing and deploying a robust and secure IoT SSH web solution.
Security should be paramount when using IoT SSH web solutions. Implementing robust authentication mechanisms, regularly updating software, and monitoring for security vulnerabilities are all crucial steps. For instance, the system might even clean up the key immediately after a successful login attempt, so that a new public key setup is required for the next login attempt by the same user, adding an extra layer of security. This proactive approach to security helps to protect your IoT devices from unauthorized access and malicious attacks.
Simple SSH login through a web UI (User Interface) offers a convenient and user-friendly way to access your IoT devices. Instead of using a command-line interface, users can log in to their devices through a web browser, making it easier to manage and control them. This is particularly useful for users who are not familiar with command-line tools. Furthermore, web UIs can be customized to provide a more intuitive and visually appealing interface for interacting with IoT devices.
Integrating RealVNC or other VNC (Virtual Network Computing) software allows users to access and control a remote desktop on their IoT devices. This is particularly useful for devices that have a graphical user interface (GUI). By using VNC, users can remotely access the device's desktop and interact with applications as if they were physically present. This feature enhances the manageability of IoT devices and provides a more immersive user experience.
SSH port forwarding with Qbee VPN (Virtual Private Network) provides a secure and reliable way to access IoT devices behind firewalls. Qbee VPN creates a secure tunnel between the user and the IoT device, allowing for remote access and control. SSH port forwarding enables users to forward specific ports from the IoT device to their local machine, allowing them to access services running on those ports. This combination of VPN and port forwarding provides a secure and flexible way to manage IoT devices remotely.
Monitoring device metrics and inventory is essential for maintaining the health and performance of your IoT deployments. By tracking key metrics such as CPU usage, memory utilization, and network traffic, users can identify anomalies and proactively address potential issues. Device inventory management helps to keep track of all the IoT devices in your network, including their hardware and software configurations. This information is invaluable for troubleshooting problems and ensuring that all devices are running the latest software versions.
Using IoT device metrics to identify anomalies is a crucial aspect of proactive system management. By establishing baseline performance metrics for your IoT devices, you can quickly detect deviations from the norm and investigate potential problems. For example, a sudden spike in CPU usage or a drop in network traffic could indicate a security breach or a hardware failure. By monitoring these metrics in real-time, you can identify and address issues before they impact the performance of your IoT deployments.
- Aayushi Jaiswal The Rising Star Of Bollywood Whos Capturing Hearts
- Bollyflix Your Ultimate Guide To Bollywood Movies Online

Download Remote IoT Platform SSH For Free On Mac The Ultimate Guide

Remote IoT Web SSH Download Comprehensive Guide To Secure Access And
Unlocking The Power Of IoT SSH Web Free Android A Comprehensive Guide